STEGOsaurus

1. What's the file name of the second file? With file extension.
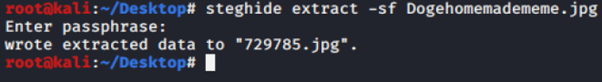
2. What's the second flag?
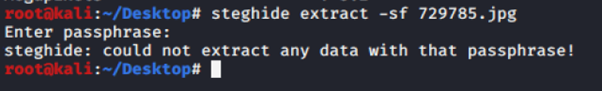

Last updated





Last updated
steghide extract -sf Dogehomemadememe.jpg