CTF collection Vol.1
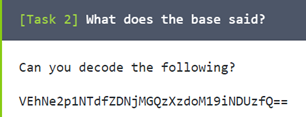
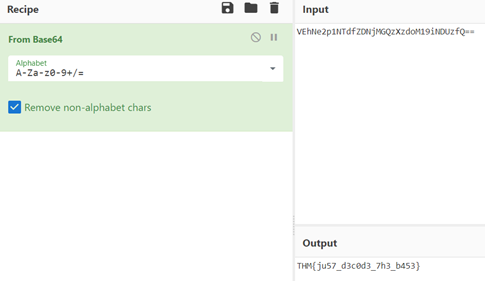
1. What does the base said?
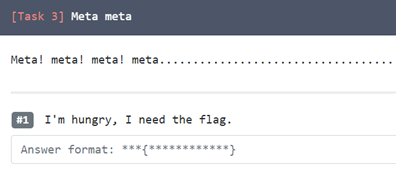
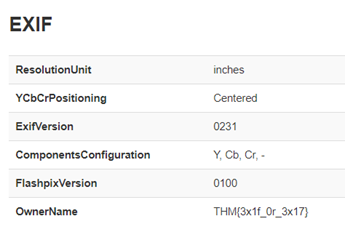
2. Meta Meta

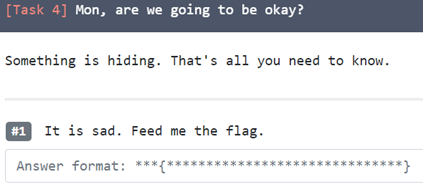
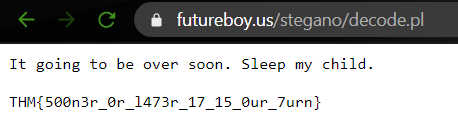
3. Mon, are we going to be okay

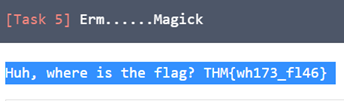
4. Erm......Magick
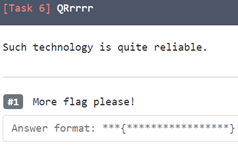
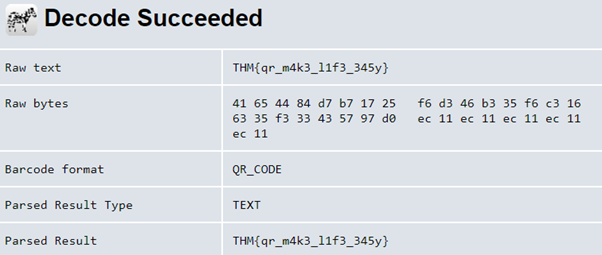
5. QRrrrr
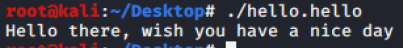
6. Reverse it or read it?
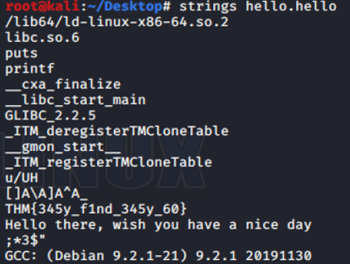
7. Another decoding stuff
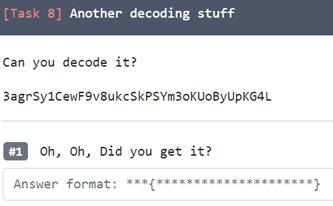
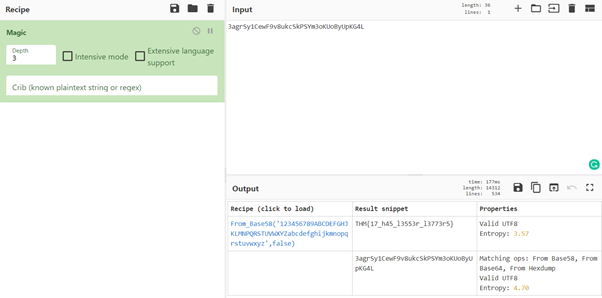
8. Left or right
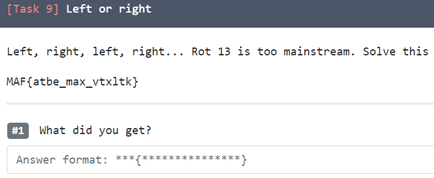
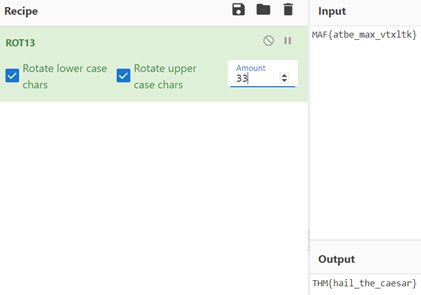
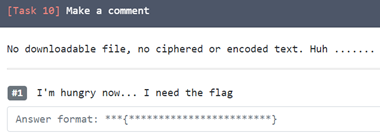
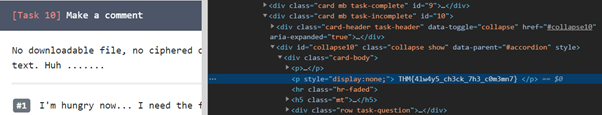
9. Make a comment
10. Can you fix it?
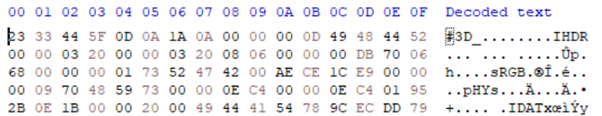
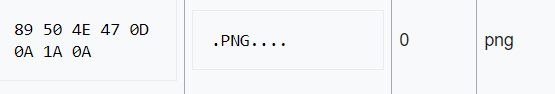
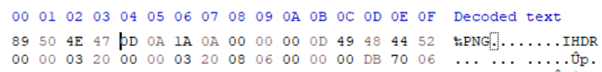

11. Read it
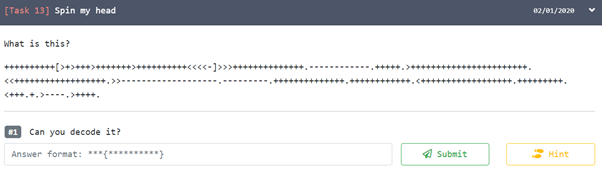
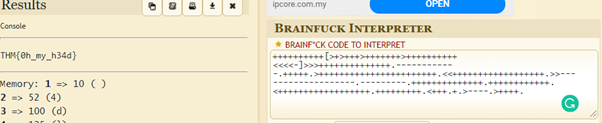
12. Spin my head
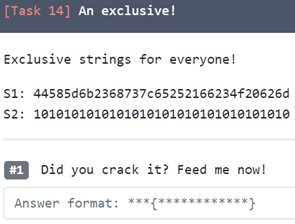
13. An exclusive!
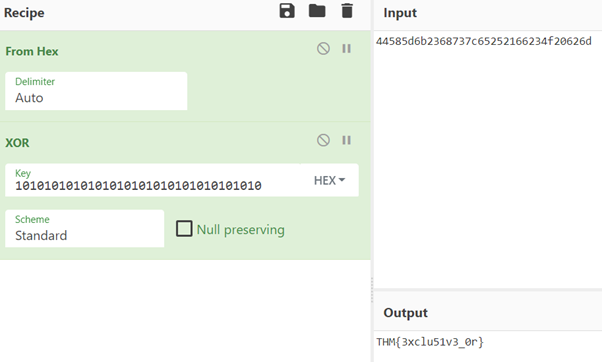
14. Binary Walk
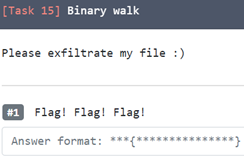
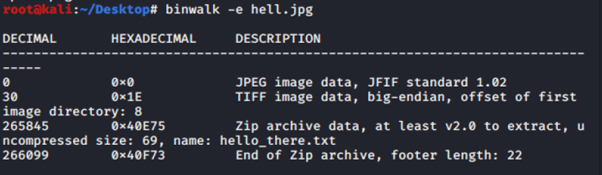
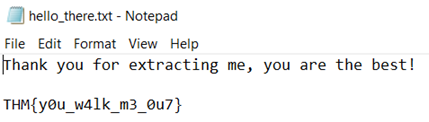
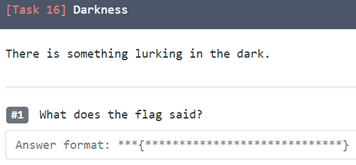
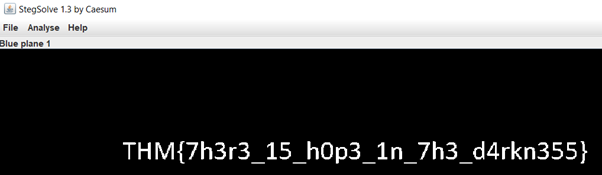
15. Darkness
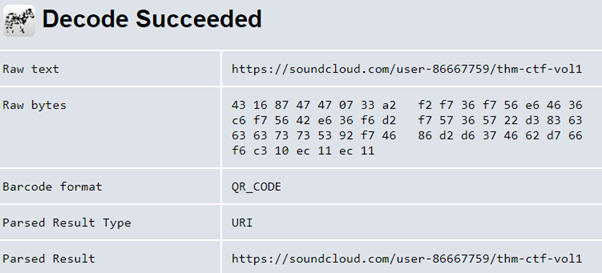
16. A sounding QR
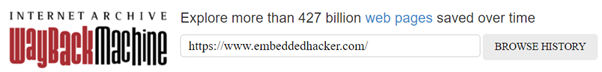
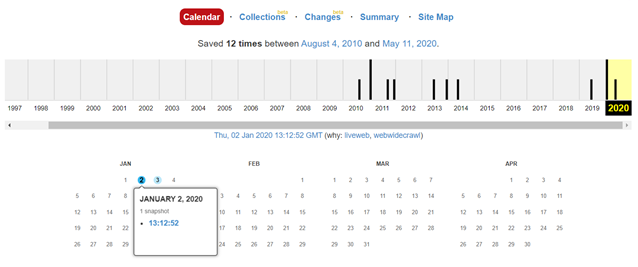
17. Dig up the past
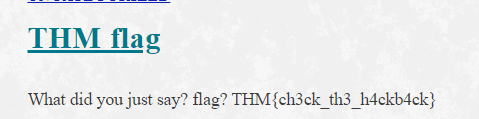
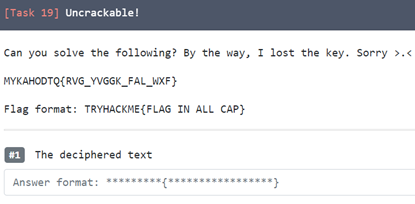
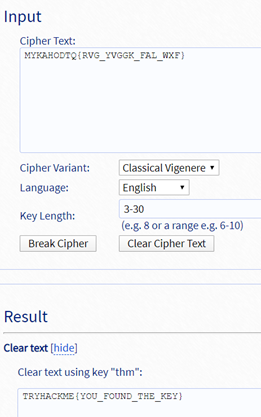
18. Uncrackable!
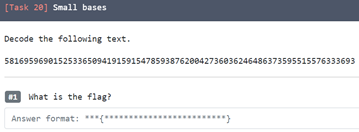
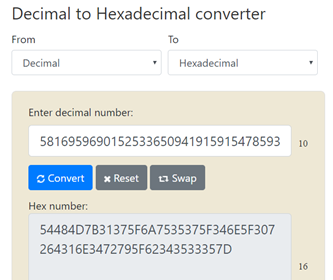
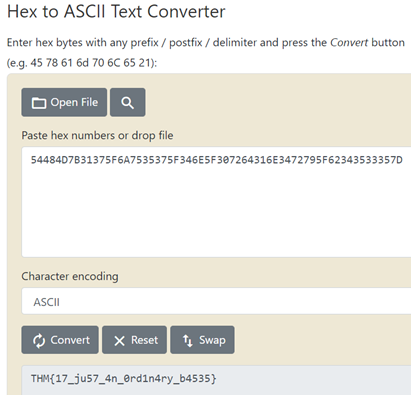
19. Small Bases
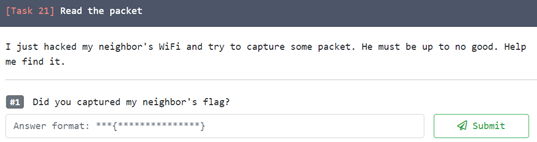
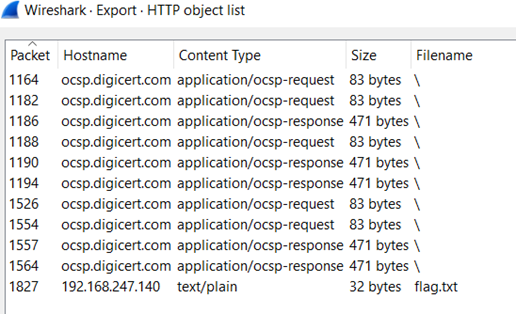
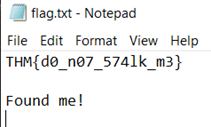
20. Read the packet
Last updated