Wonderland
Penetration Testing Methodology
Walkthrough - There is so many rabbit hole. Watch out.




Last updated










Last updated
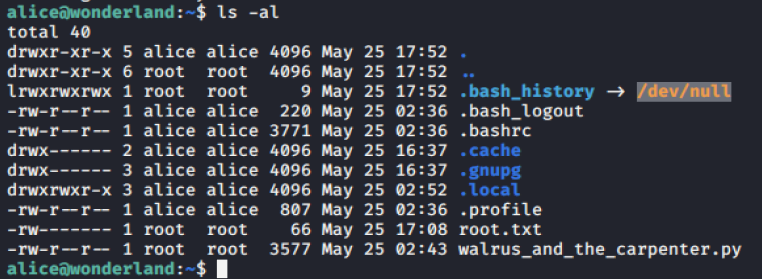
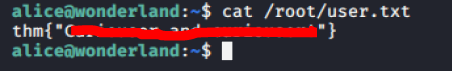
nmap -A 10.10.177.100gobuster dir -u http://10.10.177.100/ -w /root/List/directory-list-2.3-medium.txt -t 80 -x .txt,.php,.htmldirbusterssh *****@10.10.177.100ls -alcat /root/user.txt