HOLO

.NET basics
Web application exploitation
AV evasion
Whitelist and container escapes
Pivoting
Operating with a C2 (Command and Control) Framework
Post-Exploitation
Situational Awareness
Active Directory attacks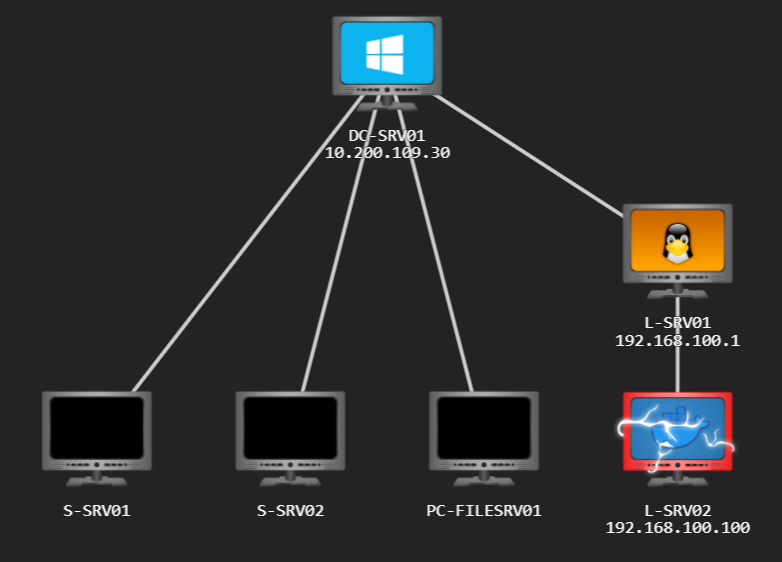
Last updated

.NET basics
Web application exploitation
AV evasion
Whitelist and container escapes
Pivoting
Operating with a C2 (Command and Control) Framework
Post-Exploitation
Situational Awareness
Active Directory attacks
Last updated
Misconfigured sub-domains
Local file Inclusion
Remote code execution
Docker containers
SUID binaries
Password resets
Client-side filters
AppLocker
Vulnerable DLLs
Net-NTLMv2 / SMB