Day 6 - Data Elf-iltration
Q1 - What data was exfiltrated via DNS?
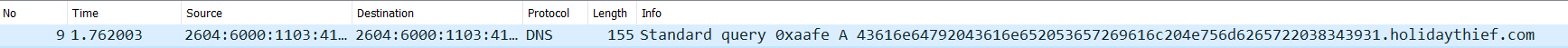
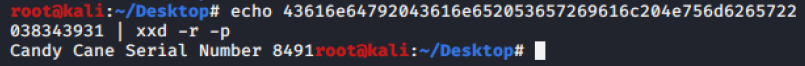
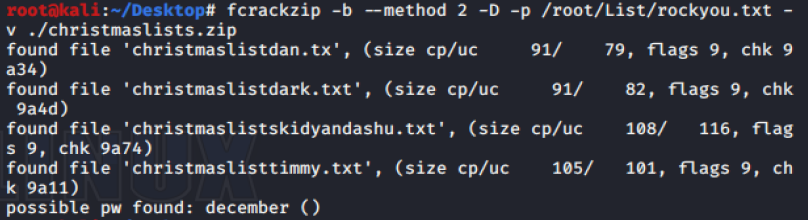
Q2 - What did Little Timmy want to be for Christmas?
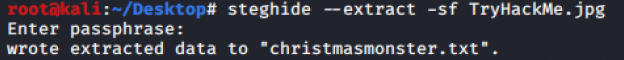
Q3 - What was hidden within the file?
Last updated